Conditional Access Policy - Block Legacy Authentication
Legacy protocols like POP, SMTP and IMAP don't support MFA and can be used to password spray attack your Office 365 mailboxes. You can disable legacy authentication and improve your Office 365 security using this Azure Conditional Access policy.
Blocking legacy authentication in Office 365
Applications that use legacy authentication do not support two factor authentication and so are vulnerable to password spray attacks. Some protocols that use basic authentication are: SMTP, IMAP, POP, Exchange Web Services (EWS), Exchange ActiveSync (EAS)
- Blocking legacy authentication will block older clients that do not use modern authentication
- You should add exceptions for any mailboxes that need to use legacy protocols otherwise they will stop working when the policy is applied
- It can take up to 24 hours for the conditional access policy to take effect
- If you have security defaults enabled then a policy to block legacy authentication will already be configured
Check if legacy authentication is enabled in Office 365
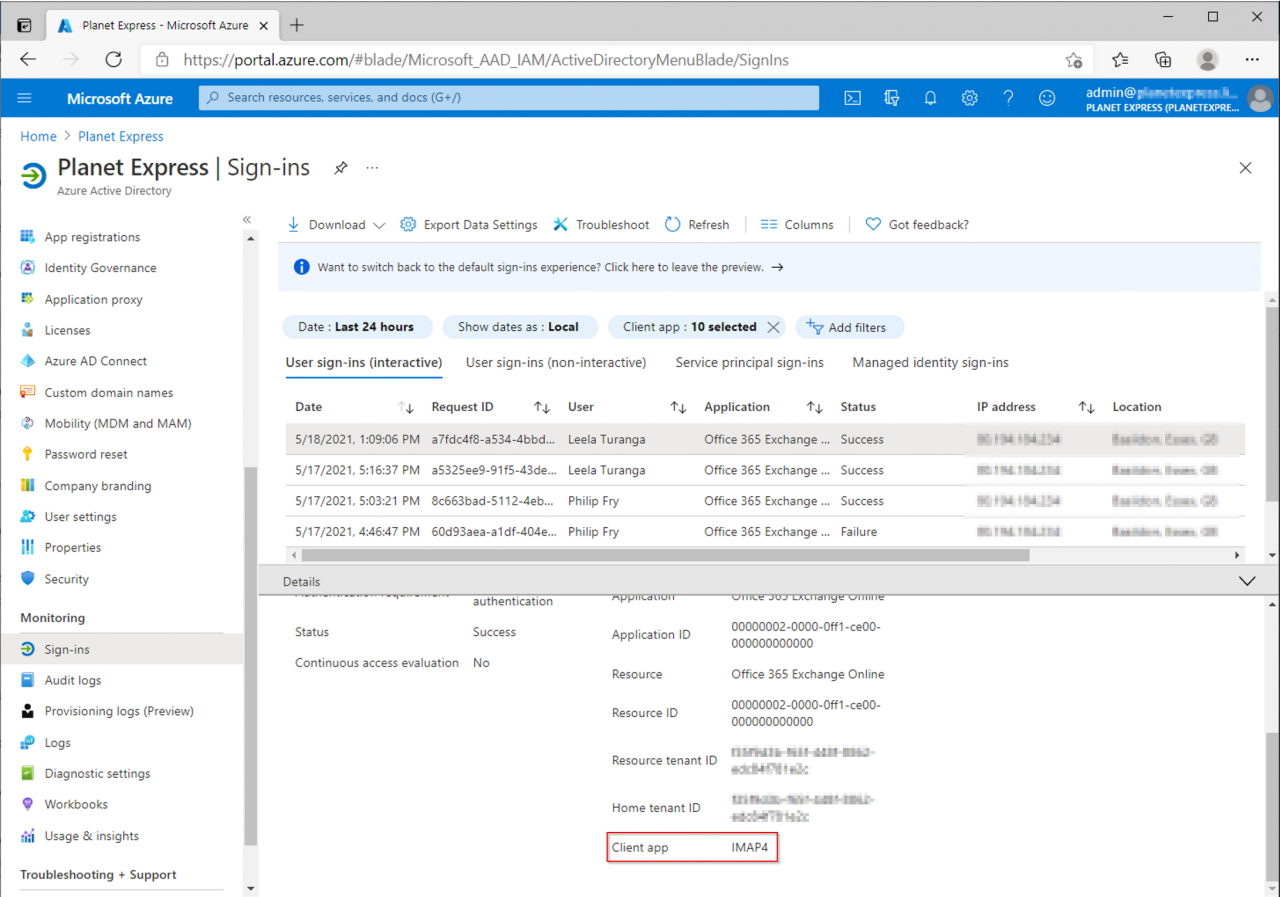
You can check the Azure AD sign-in logs to find clients that are still using legacy authentication
Azure Active Directory
Monitoring - Sign-ins
Use the Client app filter to look for legacy authentication clients - tick all the legacy clients
Select one of the sign-ins then click the Basic info tab
You can see the Client app is IMAP
Test if IMAP and SMTP are enabled using Outlook
Let's do a quick test to check if IMAP and SMTP are enabled for a mailbox. This way we can repeat the test after creating the Conditional Access Policy to confirm that IMAP and SMTP are disabled.
Create a new Outlook profile using these settings to connect to the mailbox using IMAP and SMTP
Office 365 IMAP Settings
Incoming mail server (IMAP) outlook.office365.com
IMAP port 993
IMAP security SSL
Office 365 SMTP Settings
Outgoing mail server (SMTP) smtp.office365.com
SMTP port 587
SMTP security TLS
Outgoing server (SMTP) requires authentication
We've successfully connected to the mailbox using IMAP and SMTP
Conditional Access Policy to block legacy authentication
Sign into the Azure Portal
Microsoft Azure Portal
https://portal.azure.com
Create a new policy
Azure Active Directory
Security - Conditional Access - New Policy
Name Block Legacy Authentication
Users and groups
Include: All Users
Exclude: your admin account
Cloud apps or actions
Include: All cloud apps
Conditions
Client apps
Configure Yes
Legacy authentication clients
Tick Exchange ActiveSync clients, Other clients
Access controls - Grant
Block Access
Enable the policy in Report-only mode
Monitor Azure Active Directory sign-ins
Enable the policy in report-only mode so you can monitor the Azure AD sign-in logs and check that the policy is working as expected.
In this example we can see the IMAP client connection
The report-only tab allows us to check what would happen if the policy was enabled
Report-only - more - show details
Client app IMAP
Grant controls block
This example shows that the IMAP client access has been blocked
Once you're happy that the policy is working OK, you can enable it
Test if IMAP and SMTP are now disabled using Outlook
Let's try re-connecting to the mailbox using IMAP and SMTP with the Outlook profile we created earlier, this will confirm that the conditional access policy is now working and IMAP and SMTP are blocked
Test Account Settings
Connecting to the mailbox using IMAP now doesn't work - we get repeatedly prompted for a username and password
Failed to connect to the mailbox using IMAP and SMTP




















Comments