OPNsense NAT port forward rules with NAT reflection (Loopback/Hairpin)
How to configure OPNsense firewall NAT port forward rules with NAT reflection (Loopback/Hairpinning) for web servers
What is NAT reflection, and why would you enable it?
NAT reflection allows clients inside your network to access web servers using the servers external WAN IP address. NAT reflection redirects client requests to the web server's internal IP address.
This means that firewall rules meant for external traffic are not applied and you don't have to manage internal DNS entries for your web server.
OPNsense port forward rules with NAT reflection
Create inbound firewall rules for web server allowing HTTP port 80 and HTTPS port 443 with NAT reflection/hairpinning
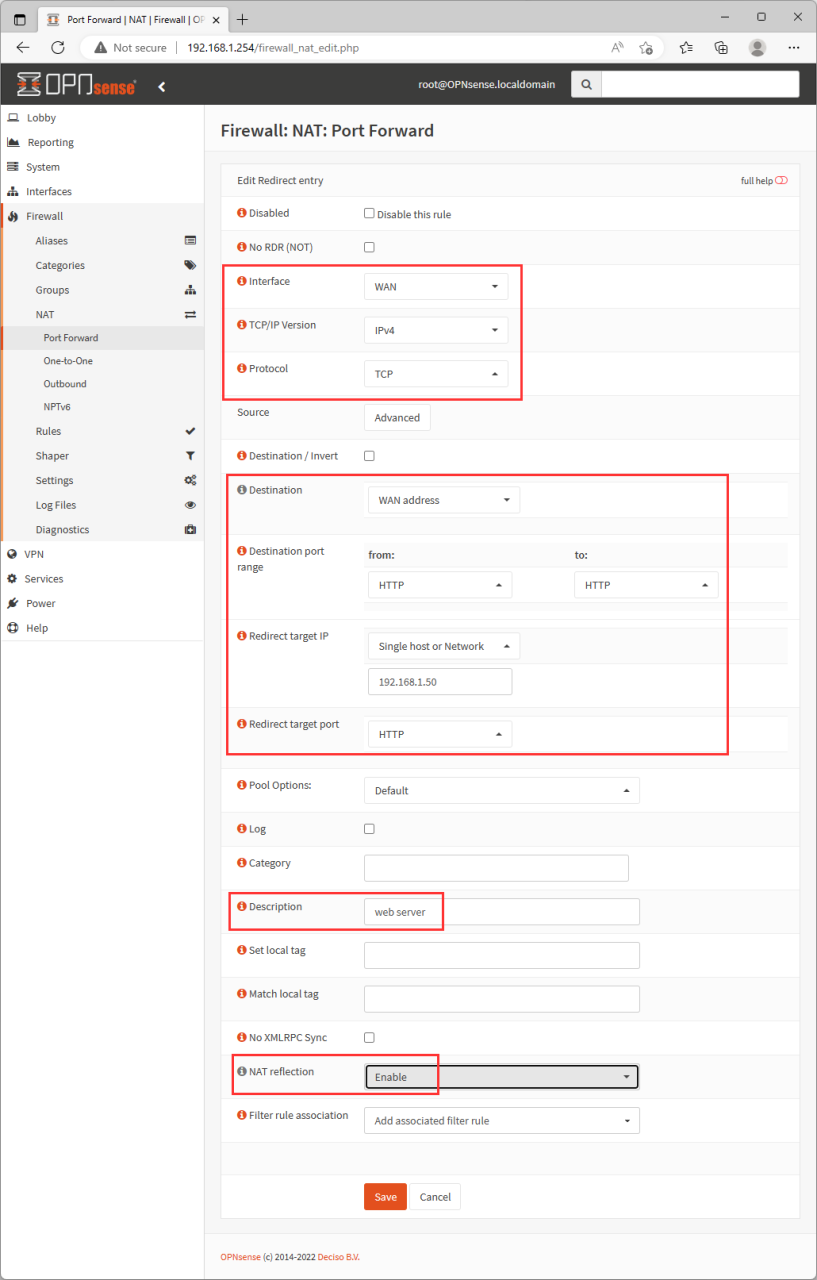
Firewall - NAT - Port Forward - Add
Example: OPNsense NAT port foward rule for HTTP
Interface: WAN
TCP/IP version: IPv4
Protocol: TCP
Destination: WAN address
Destination port range: HTTP
Redirect target IP: single host/network IP 192.168.1.50
Redirect target port: HTTP
Description: web server
NAT reflection: Enable
Save and apply changes
Example: OPNsense NAT port foward rule for HTTPS
Repeat the steps to create a port forwarding rule for HTTPS
Interface: WAN
TCP/IP version: IPv4
Protocol: TCP
Destination: WAN address
Destination port range: HTTPS
Redirect target IP: single host/network IP 192.168.1.50
Redirect target port: HTTPS
Description: web server
NAT reflection: Enable
Save and apply changes
Reference:
by Author
OPNsense docs - Network Address Translation
https://docs.opnsense.org/manual/nat.html




Comments 3
need to enable lan interface as well.
Excellent tutorial! I was having a hard time figuring out how to use that address inside my network as well as outside using NGINX. I managed to access it from outside, but OPNSense was blocking using the same address when inside my network. NAT Reflection set to "Enable" instead of Default was the issue! Thanks for your help.
Thanks for taking the time to comment. I’m glad you found the guide helpful!