Automatically install updates using unattended-upgrades on Debian 11
How to install and configure unattended-upgrades for automatically installing security updates and other package updates on Debian 11
Table of Contents
Install unattended-upgrades
Unattended upgrades configuration files
Configure unattended upgrade settings
Configure automatic reboots
Remove unused dependencies
Set up email notifications
Schedule automatic updates
Change the upgrade scheduled time
Test unattended upgrades
Unattended upgrades log files
Unattended upgrade is not updating some packages
Allow installing updates from all origins
Automatically install updates using unattended-upgrades
Regularly installing updates is essential to keep your servers up to date with the latest software and security patches. The unattended-upgrades package is used to automatically install security and other package updates on Debian servers. Updates can be scheduled, and servers automatically rebooted. Then apt-listchanges will send an email notification to let you know which packages have been changed.
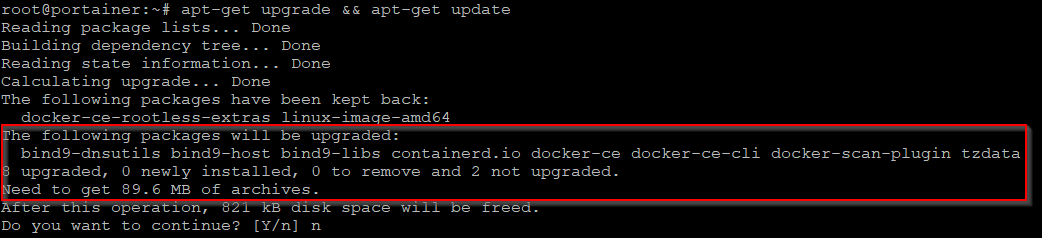
In this example, running apt-get upgrade shows package updates need to be installed
apt-get upgrade && apt-get update
Install unattended-upgrades
Install unattended-upgrades, apt-listchanges and apt-config-auto-update
- unattended-upgrades is used to automatically install updates
- apt-listchanges will send an email notification about packages that have been changed
- apt-config-auto-update is required for automatic reboots after updates have been installed
# install unattended-upgrades, apt-listchanges and apt-config-auto-update apt-get install unattended-upgrades apt-listchanges apt-config-auto-update
Unattended upgrades configuration files
Unattended upgrades uses these configuration files:
/etc/apt/apt.conf.d/50unattended-upgrades
Main configuration file for unattended-upgrades
/etc/apt/apt.conf.d/20auto-upgrades
Used to configure how often automatic updates run
/etc/apt/listchanges.conf
Configuration file for email notifications using apt-listchanges
Configure unattended upgrade settings
Edit the file /etc/apt/apt.conf.d/50unattended-upgrades to change the settings for unattended-upgrades
- Configuration options are commented out using //
- The default settings are to install Debian-Security updates automatically
- Debian updates should also be enabled by removing the comment // from the line
nano /etc/apt/apt.conf.d/50unattended-upgrades
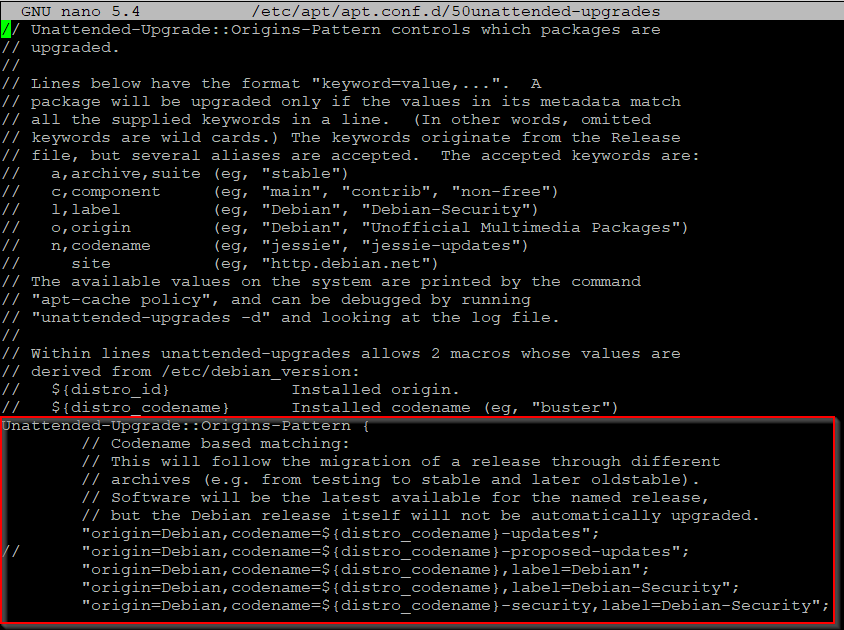
Remove the comment // from this line to enable Debian updates as well as the default security updates
"origin=Debian,codename=${distro_codename}-updates";
Unattended-Upgrade::Origins-Pattern {
// Codename based matching:
// This will follow the migration of a release through different
// archives (e.g. from testing to stable and later oldstable).
// Software will be the latest available for the named release,
// but the Debian release itself will not be automatically upgraded.
"origin=Debian,codename=${distro_codename}-updates";
// "origin=Debian,codename=${distro_codename}-proposed-updates";
"origin=Debian,codename=${distro_codename},label=Debian";
"origin=Debian,codename=${distro_codename},label=Debian-Security";
"origin=Debian,codename=${distro_codename}-security,label=Debian-Security";
When you've finished editing, the Unattended-Upgrade::Origins-Pattern section of the file should look something like this.
Configure automatic reboots
Remove the comments // from these lines in the 50unattended-upgrades file and change Unattended-Upgrade::Automatic-Reboot to "true" to enable automatic reboots.
nano /etc/apt/apt.conf.d/50unattended-upgrades
// Automatically reboot *WITHOUT CONFIRMATION* if // the file /var/run/reboot-required is found after the upgrade Unattended-Upgrade::Automatic-Reboot "true"; // Automatically reboot even if there are users currently logged in // when Unattended-Upgrade::Automatic-Reboot is set to true Unattended-Upgrade::Automatic-Reboot-WithUsers "true";
Remove unused dependencies
When packages are installed, apt-get will also install other software that the application depends on. The dependencies are not automatically removed when you remove the application unless you run apt-get autoremove. This can use up disk space, especially in the case of Linux kernel updates.
Here you can see that old kernel versions have been kept in the /boot folder.
# list contents of boot directoryls /boot
# show the disk space used for the boot directorydu -sh /boot
You can enable the Remove-Unused-Dependencies option in the 50unattended-upgrades file to remove unused packages. This is the same as running apt-get autoremove.
There is also a separate option to remove unused kernel packages Remove-Unused-Kernel-Packages.
nano /etc/apt/apt.conf.d/50unattended-upgrades
// Remove unused automatically installed kernel-related packages // (kernel images, kernel headers and kernel version locked tools). Unattended-Upgrade::Remove-Unused-Kernel-Packages "true"; // Do automatic removal of newly unused dependencies after the upgrade Unattended-Upgrade::Remove-New-Unused-Dependencies "true"; // Do automatic removal of unused packages after the upgrade // (equivalent to apt-get autoremove) Unattended-Upgrade::Remove-Unused-Dependencies "true";
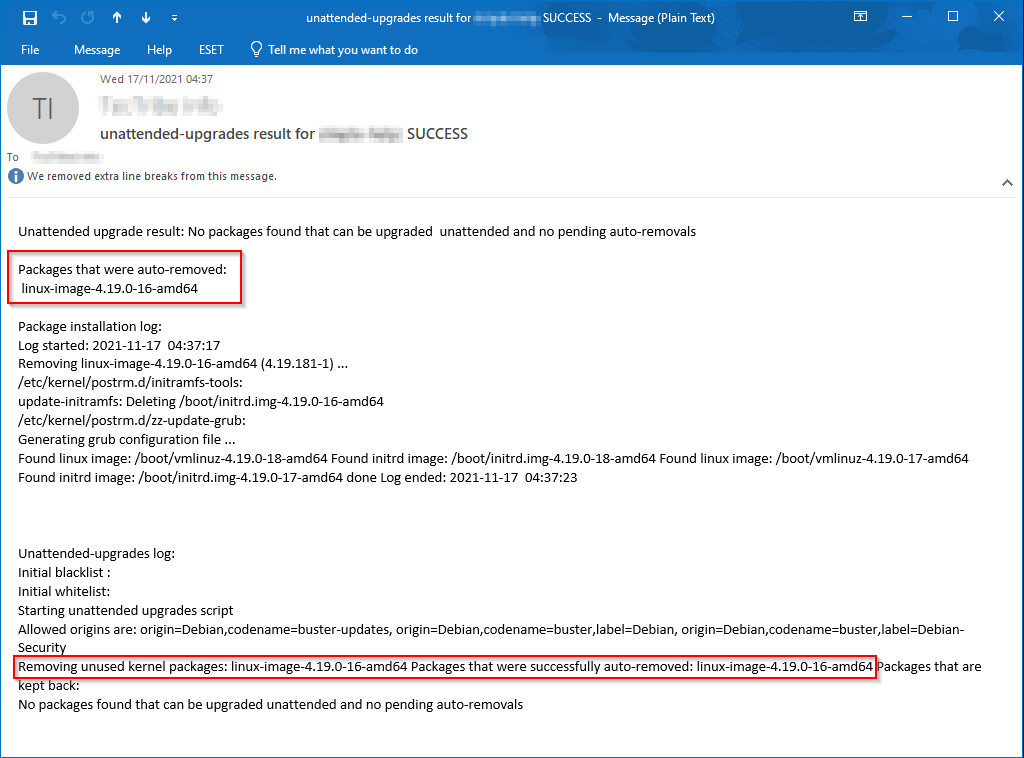
You will get an email notification that packages have been auto-removed
Checking the contents of the boot directory again shows that the old kernel linux-image-4.19.0-16-amd64 has been removed
# list contents of boot directoryls /boot
# show the disk space used for the boot directorydu -sh /boot
Set up email notifications
You can follow this guide for setting up msmtp to forward system emails to an SMTP server or email provider

Install msmtp for forwarding system emails on Debian - TechLabs
Edit the 50unattended-upgrades file, uncomment this line and enter your email address
nano /etc/apt/apt.conf.d/50unattended-upgrades
// Send email to this address for problems or packages upgrades // If empty or unset then no email is sent, make sure that you // have a working mail setup on your system. A package that provides // 'mailx' must be installed. E.g. "user@example.com" Unattended-Upgrade::Mail "EMAIL@DOMAIN.COM";
You'll also need to edit the apt-listchanges config file and add your email address
nano /etc/apt/listchanges.conf
[apt] frontend=pager which=news email_address=EMAIL@DOMAIN.COM email_format=text confirm=false headers=false reverse=false save_seen=/var/lib/apt/listchanges.db
Schedule automatic updates
The file /etc/apt/apt.conf.d/20auto-upgrades is used to configure how often automatic updates run.
Create a new file and enter the following settings to install updates daily or weekly.
nano /etc/apt/apt.conf.d/20auto-upgrades
Example: Install updates daily
APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1";
Example: Install updates weekly
APT::Periodic::Update-Package-Lists "7"; APT::Periodic::Unattended-Upgrade "7";
Change the upgrade scheduled time
# Check the next upgrade time systemctl status apt-daily-upgrade.timer
In this example, the next trigger time is 6:49 am
# Check the default upgrade scheduled time cat /lib/systemd/system/apt-daily-upgrade.timer
The default upgrade time is 6am every day
You can change the scheduled upgrade time by creating a new systemd timer
Run this command to create a new systemd timer using one of the following examples
systemctl edit apt-daily-upgrade.timer
Example: Daily at 4.00am
[Timer] OnCalendar=04:00 RandomizedDelaySec=15m
Example: Every Wed at 4.00am
[Timer] OnCalendar=Wed *-*-* 4:00 RandomizedDelaySec=15m
# Restart the upgrade timer systemctl restart apt-daily-upgrade.timer # Check the next upgrade trigger time systemctl status apt-daily-upgrade.timer
The next trigger time has now changed to 4.30am
Test unattended upgrades
You can use these options for testing unattended-upgrades
unattended-upgrades --dry-run
Just simulate installing updates, do not actually do it
unattended-upgrades --debug
Extra debug output into /var/log/unattended-upgrades.log
Unattended upgrades log files
/var/log/unattended-upgrades
unattended-upgrades-dpkg.log
unattended-upgrades.log
unattended-upgrades-shutdown.log
tail -20 /var/log/unattended-upgrades/unattended-upgrades.log
Unattended upgrade is not updating some packages
You might get this message when running unattended upgrade
No packages found that can be upgraded unattended and no pending auto-removals
Package elasticsearch has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package grafana has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package kibana has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package tzdata has a higher version available, checking if it is from an allowed origin and is not pinned down.
Running apt-get update && apt-get upgrade manually shows that there are three packages to be upgraded but unattended upgrades will not automatically download and install them
Running apt list --upgradable also shows that there are three packages that can be updated
# list packages to be upgraded apt list --upgradable
Unattended upgrades is not automatically downloading and installing these updates because they are not included in the default Debian update repositories.
To fix this, we'll need to allow updates from all origins, which will allow automatic updates from all package sources.
Allow installing updates from all origins
The Origins-Pattern in /etc/apt/apt.conf.d/50unattended-upgrades is used to specify allowed package sources. Only packages from repositories matching the allowed patterns will be upgraded
The file itself has a good explanation of the examples, or you can refer to the documentation linked at the end of this guideThe default settings are to allow updates from Debian sources. If you have installed packages from other sources, they will not get updated unless you specifically allow the repositories or allow all sources.
You can useapt-cache policy to view the options for available sources that can be used to configure settings in the 50unattended-upgrades config fileTo allow installing from all apt sources or repositories, you will need to override the default configuration. You can do this by creating a new file containing the changes with a number higher than the default config file so it will be processed after the default 50unattended-upgrades
Example: Allow all origins
nano /etc/apt/apt.conf.d/51unattended-upgrades-local
Unattended-Upgrade::Origins-Pattern {
"origin=*";
};
References:
Debian Wiki - UnattendedUpgrades
https://wiki.debian.org/UnattendedUpgradesGitHub - Unattended upgrades
by Author
https://github.com/mvo5/unattended-upgrades/blob/master/README.md












Comments 3
awesome! had some problems with the new Pi OS
Thank you!!
I have been checking out a few of your stories and I can state pretty good stuff. I will definitely bookmark your blog
Thanks for the feedback. Glad you found the guide useful!