Silently enable BitLocker using a Disk Encryption Policy with Microsoft Endpoint Manager Intune
How to silently enable BitLocker encryption and backup BitLocker keys to Azure AD using an Endpoint Manager Intune Disk Encryption Policy
Table of Contents
Requirements for BitLocker silent encryption with Intune
Check if devices support BitLocker
Testing BitLocker on Hyper-V Virtual Machine
Create Endpoint Manager Intune BitLocker policy
Hide Windows toast notifications for BitLocker
Check BitLocker Encryption Status
View BitLocker recovery keys in Endpoint Manager
Rotate BitLocker recovery keys using Endpoint Manager
BitLocker hardware requirements
- A Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware
- TPM (Trusted Platform Module) 1.2 or 2.0
- TPM 2.0 devices must have the BIOS configured for UEFI boot mode
Requirements for BitLocker silent encryption with Intune
Device requirements for silently enabling BitLocker
- Must be Azure AD Joined or Hybrid Azure AD Joined
- Device must have at least Trusted Platform Module (TPM) 1.2
Disk Encryption Policy settings for silently enabling BitLocker
These settings must be configured for silently enabling BitLocker
- Hide prompt about third-party encryption = Yes
- Allow standard users to enable encryption during Autopilot = Yes
- Device must not require use of a startup PIN or startup key
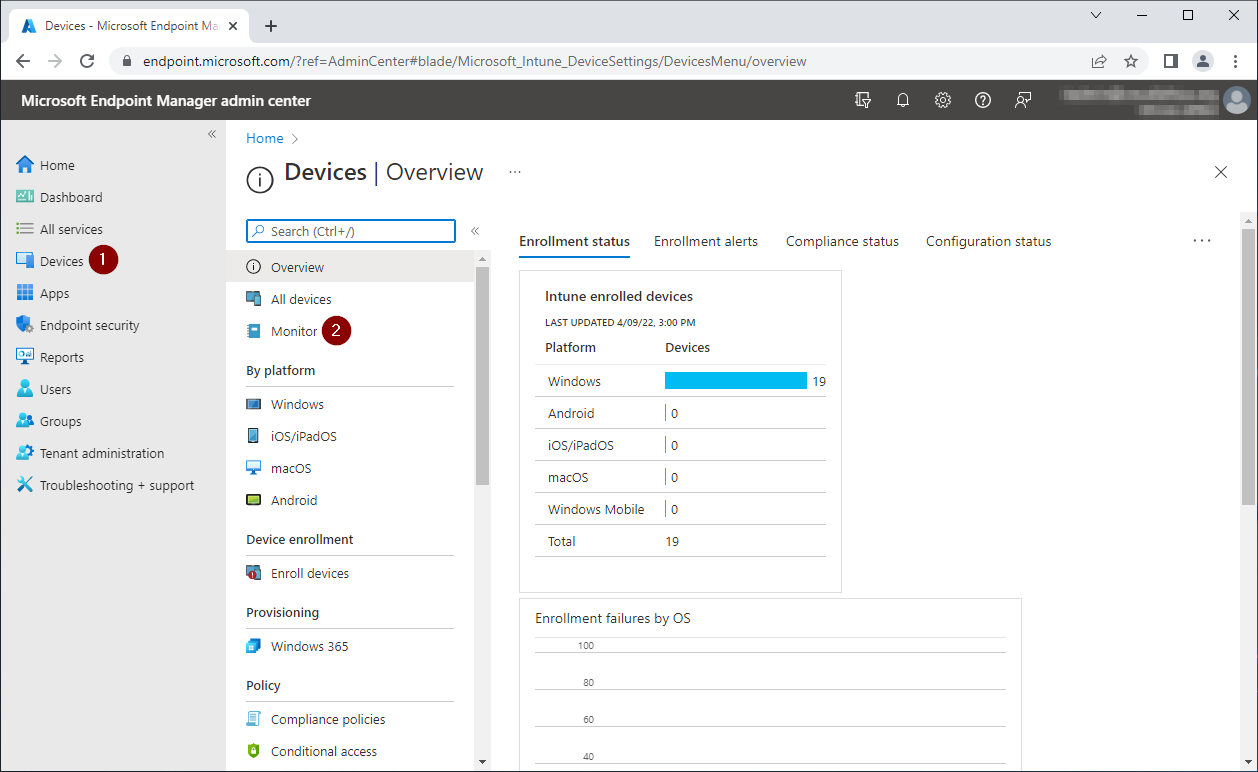
Check if devices support BitLocker
You can check your device's TPM version, encryption readiness and encryption status using the Endpoint Manager Encryption Report.
Endpoint Manager admin center
https://endpoint.microsoft.com
Devices - Monitor
Encryption Report
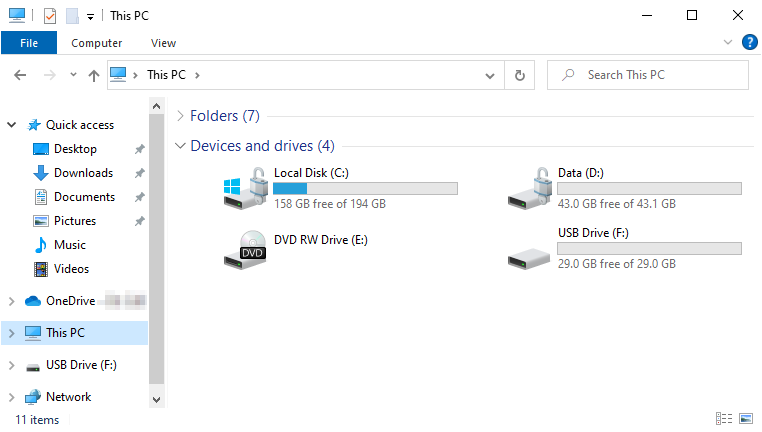
In this example, both the laptop's OS drive and fixed drive are not encrypted
Testing BitLocker on Hyper-V Virtual Machine
To test the BitLocker policy using a Hyper-V virtual machine, you'll need to enable TPM in the VM security settings
Tick - Enable Trusted Platform Module
Enable TPM on the VM using PowerShell
Enable-VMTPM -VMName "CTRLF-PC3"
Create Endpoint Manager Intune BitLocker policy
In this example, we will create a BitLocker disk encryption policy with the following settings:
- Encrypt Operating System drive and fixed drives using AES 256bit XTS
- Encrypt drive using TPM, without a pin or startup key
- Configure BitLocker silently without any user interaction
- Save BitLocker recovery keys to Azure AD
- Allow silently enabling BitLocker during Azure AD Join for users who are not local administrators
- BitLocker will only be enabled if TPM is present and usable
- BitLocker won't be enabled until recovery keys have been successfully saved to Azure Active Directory
Create new disk encryption policy
Endpoint Manager admin center
https://endpoint.microsoft.com
Endpoint Security - Disk Encryption - Create Policy
Platform: Windows 10 and later
Profile: BitLocker
Create
Name: BitLocker Policy
BitLocker - Base Settings
| Enable full disk encryption for OS and fixed data drives: Yes | Enables BitLocker encryption |
| Require storage cards to be encrypted (mobile only): Not configured | |
| Hide prompt about third-party encryption: Yes | Any warnings about drives already using third party encryption must be hidden to enable BitLocker silently. |
| Allow standard users to enable encryption during Autopilot: Yes | Allows silently enabling BitLocker during Azure AD Join for users who are not local administrators. |
| Configure client-driven recovery password rotation: Enable rotation on Azure AD and Hybrid-joined devices | BitLocker keys will automatically rotate after they are used on the client. |
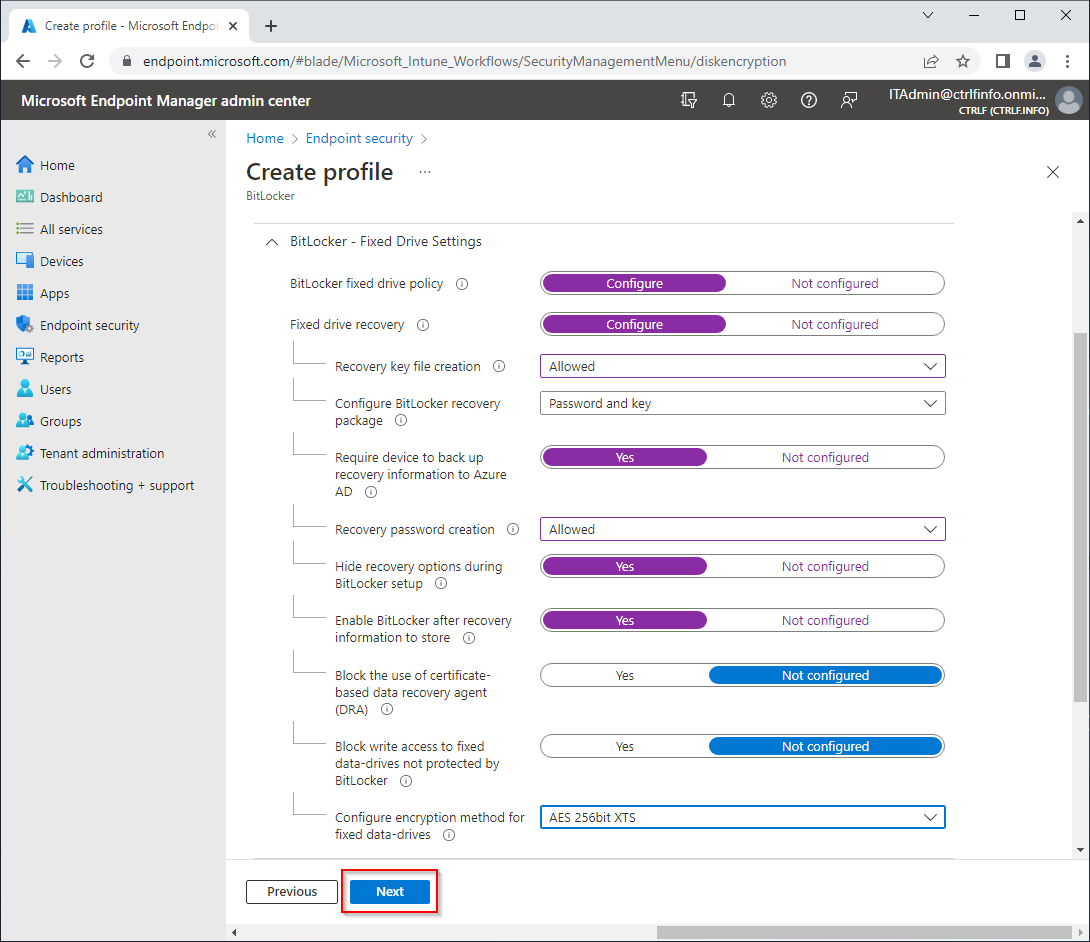
BitLocker - Fixed Drive Settings
| BitLocker fixed drive policy: Configure | Enables BitLocker encryption for fixed drives. |
| Fixed drive recovery: Configure | |
| Recovery key file creation: Allowed | Allow an admin user to create a 256-bit recovery key file manually. |
| Configure BitLocker recovery package: Password and key | Allow both BitLocker recovery password (used by admins/users to unlock protected drives) and recovery key packages (used by admins for data recovery purposes). |
| Require device to back up recovery information to Azure AD: Yes | BitLocker won't be enabled until recovery keys have been successfully saved to Azure Active Directory. Setting this to Not configured means that BitLocker encryption will complete even if the recovery key backup to Azure AD fails. |
| Recovery password creation: Allowed | Setting this to Allow will generate a 48-digit recovery password during BitLocker initialization and send it to Azure AD. For BitLocker silent encryption, this setting should be configured to Allowed or Required |
| Hide recovery options during BitLocker setup: Yes | Block users from being able to choose extra recovery options such as printing recovery keys during the BitLocker setup. This setting does not apply to silent encryption |
| Enable BitLocker after recovery information to store: Yes | When this option is set to Yes, the recovery key will be backed up to Azure AD DS. This setting is only required in an Azure hybrid services joined scenario. |
| Block the use of certificate-based data recovery agent (DRA): Not configured | |
| Block write access to fixed data-drives not protected by BitLocker: Not configured | |
| Configure encryption method for OS drives: AES 256bit XTS | Encrypt the drive using AES 256bit XTS |
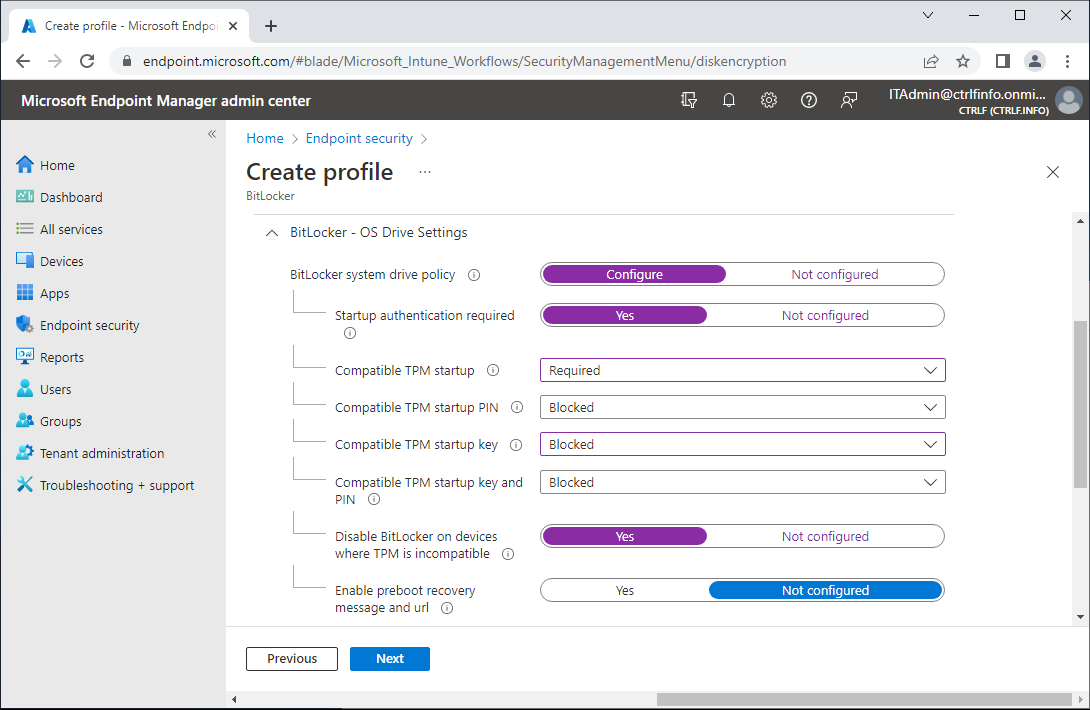
BitLocker - OS Drive Settings
| BitLocker system drive policy: Configure | Enables BitLocker encryption for OS drive |
| Startup authentication required: Yes | Allows configuring BitLocker authentication settings for system start up e.g. using Trusted Platform Module (TPM) |
| Compatible TPM startup: Required | Setting this to Require TPM will only enable BitLocker if TPM is present and usable. |
| Compatible TPM startup PIN: Blocked | PIN should be disabled to silently enable BitLocker |
| Compatible TPM startup Key: Blocked | Startup keys should be disabled to silently enable BitLocker |
| Compatible TPM startup key and PIN: Blocked | Startup keys and PIN combination should be disabled to silently enable BitLocker |
| Disable BitLocker on devices where TPM is incompatible: Yes | Disables BitLocker from being configured without a compatible TPM chip. |
| Enable preboot recovery message and url: Not configured | |
| System drive recovery: Configure | |
| Recovery key file creation: Allowed | Allow an admin user to create a 256-bit recovery key file manually. |
| Configure BitLocker recovery package: Password and key | Allow both BitLocker recovery password (used by admins/users to unlock protected drives) and recovery key packages (used by admins for data recovery purposes). |
| Require device to back up recovery information to Azure AD: Yes | BitLocker won't be enabled until recovery keys have been successfully saved to Azure Active Directory. Setting this to Not configured means that BitLocker encryption will complete even if the recovery key backup to Azure AD fails. |
| Recovery password creation: Allowed | Setting this to Allow will generate a 48-digit recovery password during BitLocker initialization and send it to Azure AD. For BitLocker silent encryption, this setting should be configured to Allowed or Required |
| Hide recovery options during BitLocker setup: Yes | Block users from being able to choose extra recovery options such as printing recovery keys during the BitLocker setup. This setting does not apply to silent encryption |
| Enable BitLocker after recovery information to store: Yes | When this option is set to Yes, the recovery key will be backed up to Azure AD DS. This setting is only required in an Azure hybrid services joined scenario. |
| Block the use of certificate-based data recovery agent (DRA): Not configured | |
| Minimum PIN length: 10 | |
| Configure encryption method for OS drives: AES 256bit XTS | Encrypt the drive using AES 256bit XTS |
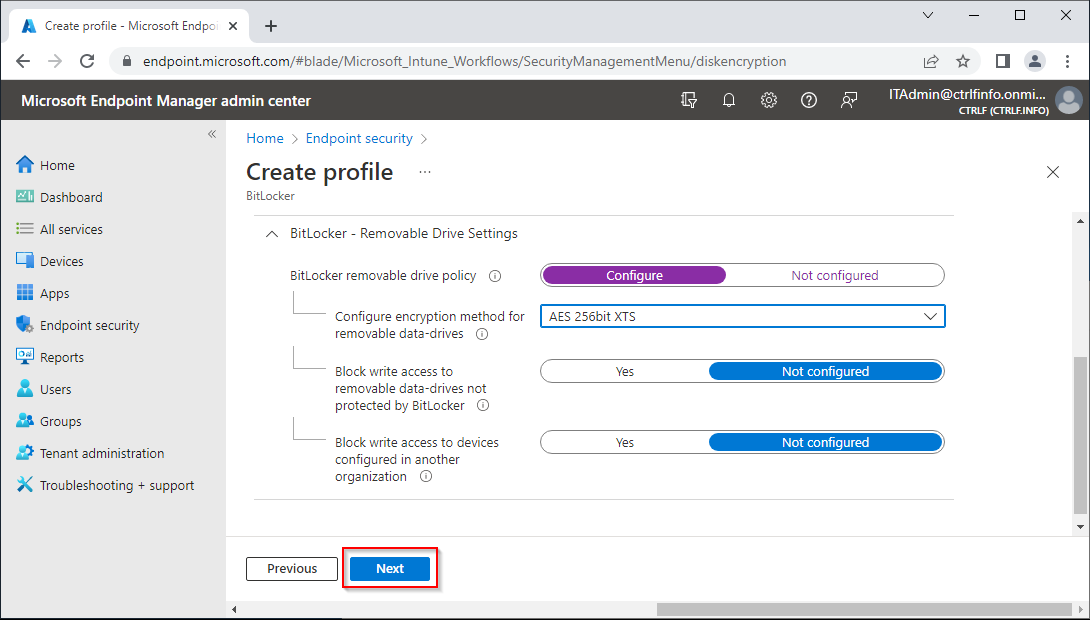
BitLocker - Removable Drive Settings
Configuring these will not enable BitLocker encryption for removable drives, but if you don't configure the encryption method, you will get this error:
"Encryption Method setting for all drive types must have a encryption type, or all drive type must be not configured."
| BitLocker - Removable Drive Settings: Configure | |
| Configure encryption method for removable data-drives: AES 256bit XTS | |
| Block write access to removable data-drives not protected by BitLocker: Not configured | |
| Block write access to devices configured in another organization: Not configured |
In this example, we are not using scope tags.
Assign disk encryption policy to test group
Click Create
Hide Windows toast notifications for BitLocker
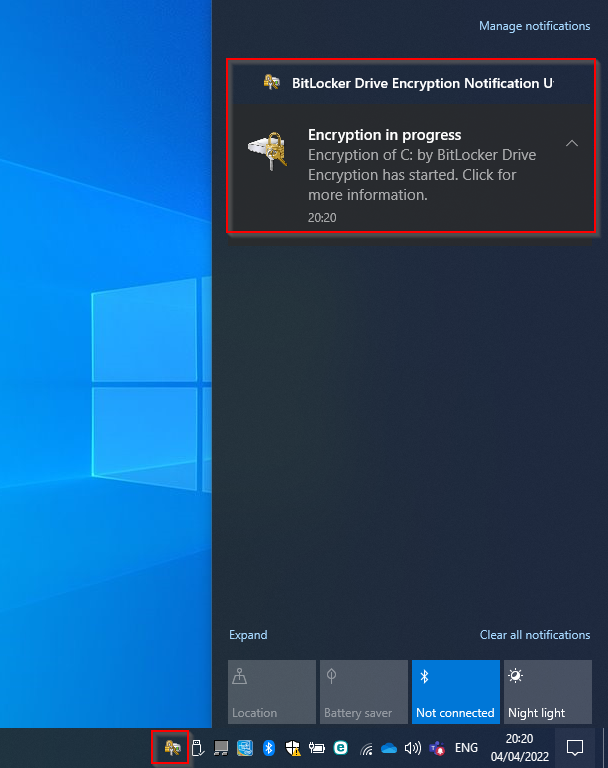
Even though the Endpoint Manager Disk Encryption policy has been configured to silently enable BitLocker, you may still see Windows toast notifications for BitLocker encryption.
Example: BitLocker "Encryption in progress" Windows toast notification
Registry key to disable BitLocker toast notifications
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Microsoft.Explorer.Notification.{4958E903-D554-EF09-81F9-13359BC57101}
"Enabled"=dword:00000000
PowerShell script to create registry key to disable BitLocker notifications
hide-bitlocker-notifications.ps1
New-Item -Path "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings" -Name "Microsoft.Explorer.Notification.{4958E903-D554-EF09-81F9-13359BC57101}" -Force
New-ItemProperty -Path "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Microsoft.Explorer.Notification.{4958E903-D554-EF09-81F9-13359BC57101}" -Name "Enabled" -Value 0 -Force
Deploy PowerShell registry script for disabling BitLocker notifications using Endpoint Manager
We can use Endpoint Manager to deploy the PowerShell script, which adds the registry key to disable BitLocker notifications.
Endpoint Manager admin center
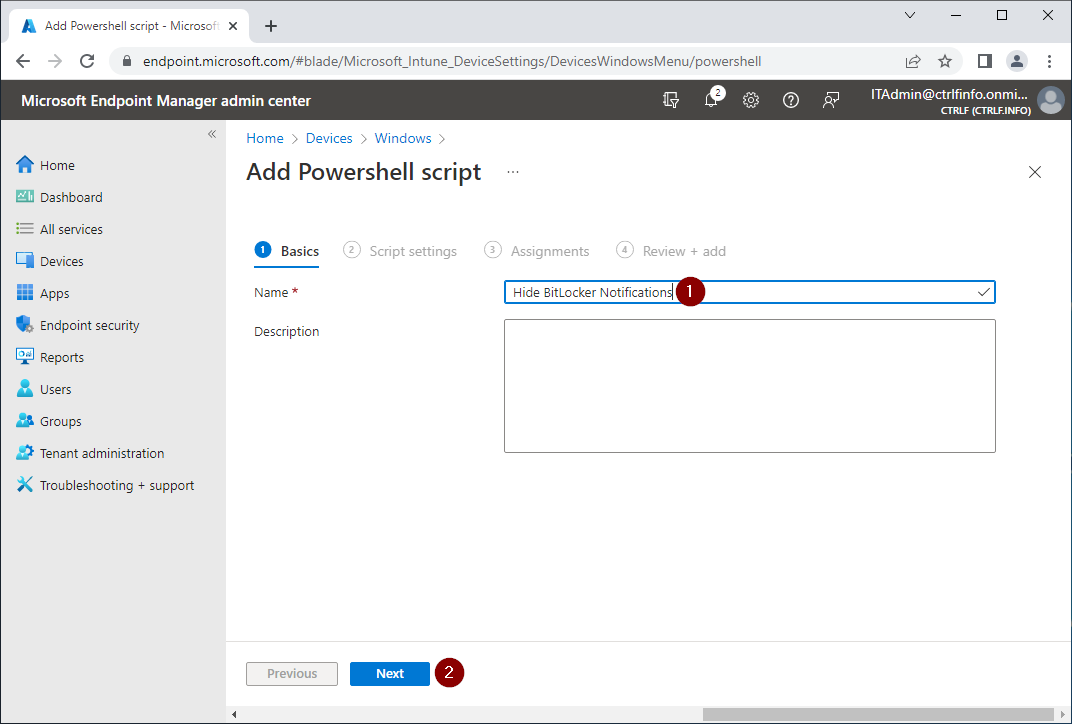
Devices - Windows - PowerShell scripts - Add
Name: Hide BitLocker Notifications
Script settings
Script location: hide-bitlocker-notifications.ps1
Run this script using the logged on credentials: Yes
Enforce script signature check: No
Run script in 64 bit PowerShell Host: Yes
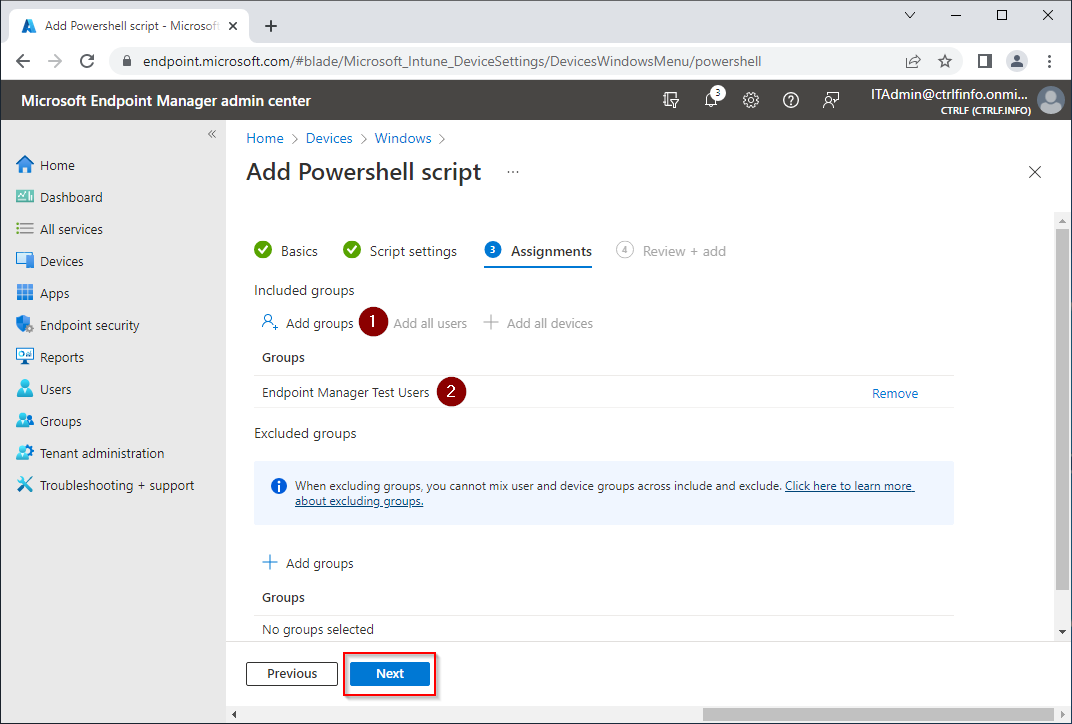
Assign the PowerShell Script to a test group of users
Add PowerShell script
Check BitLocker encryption status
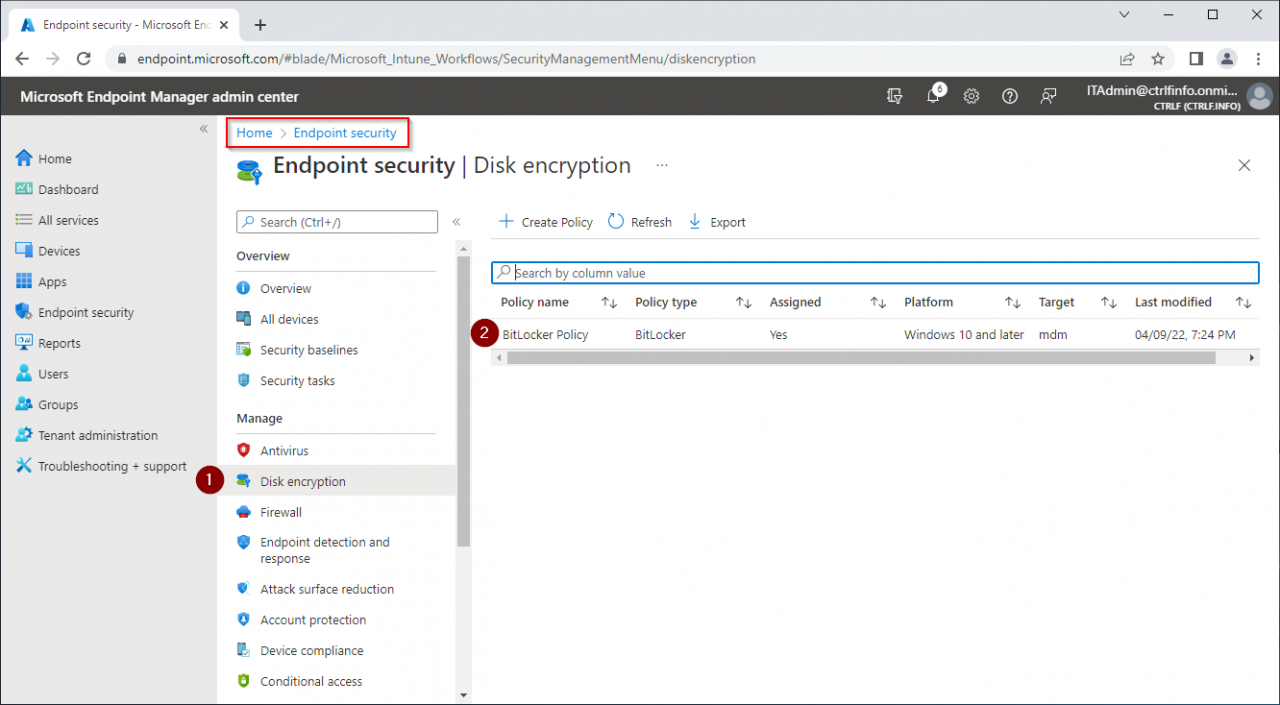
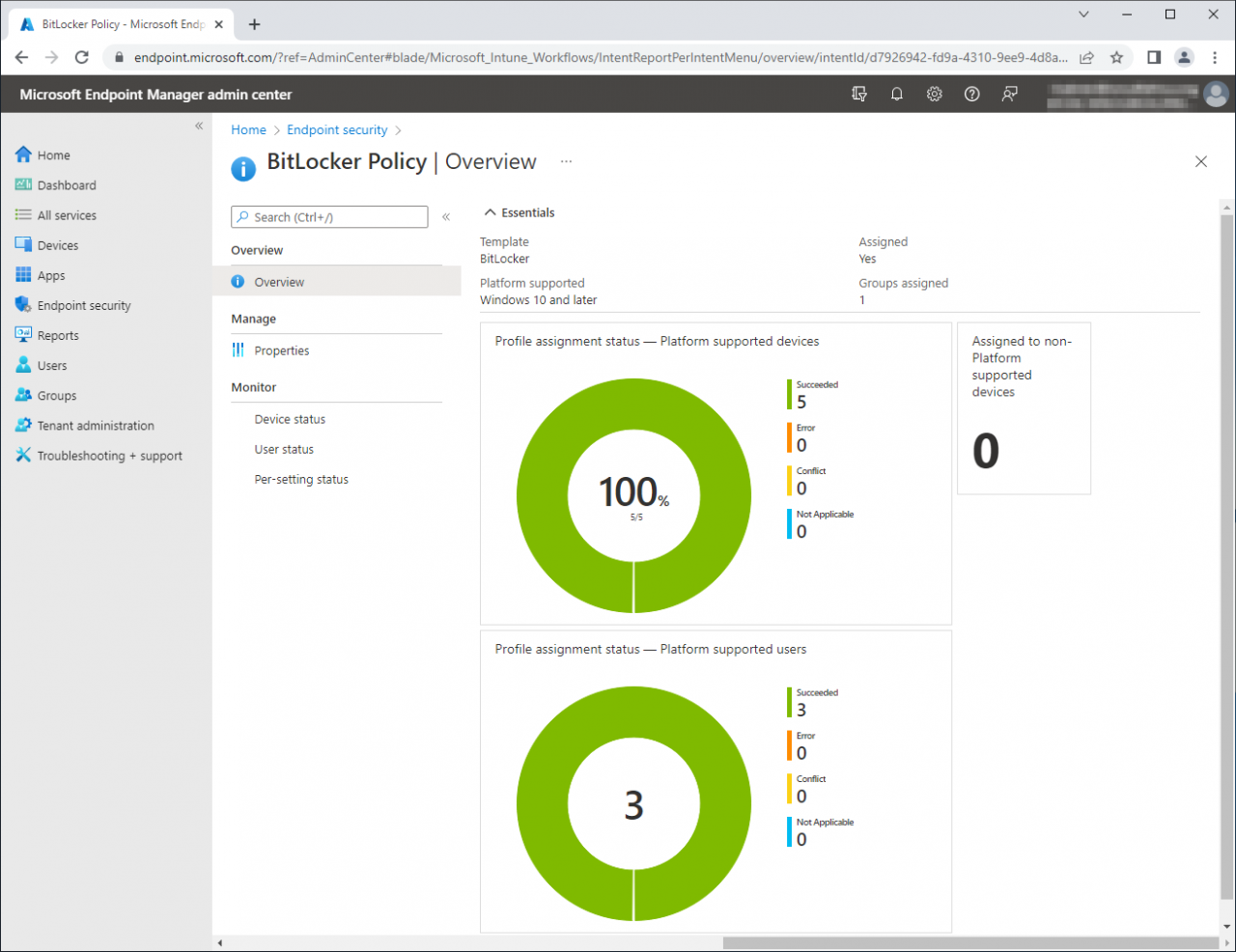
Check BitLocker Policy status in Endpoint manager
Endpoint Security - Disk Encryption - Select BitLocker policy
You can see more details about the policy settings for a device
Devices - All Devices - Select laptop
Device configuration - BitLocker policy
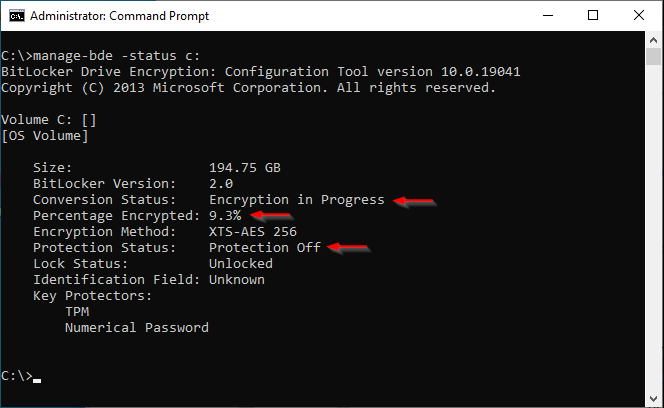
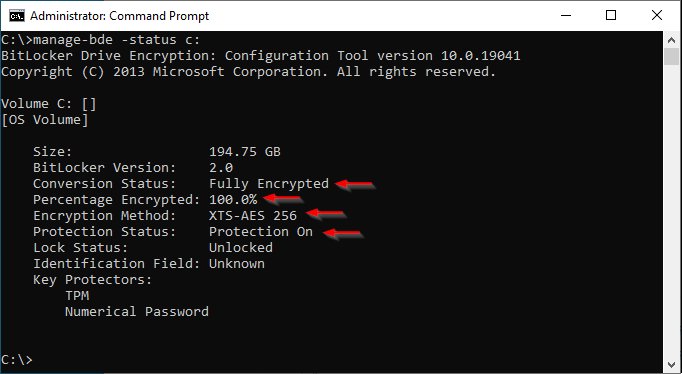
Check BitLocker status using Command Prompt manage-bde
Open Command Prompt (Run as Administrator)
manage-bde -status c:
Example: Encryption in Progress
Example: Encryption Completed
View BitLocker recovery keys in Endpoint Manager
Devices - Windows
Select device - Recovery keys - Show Recovery Key
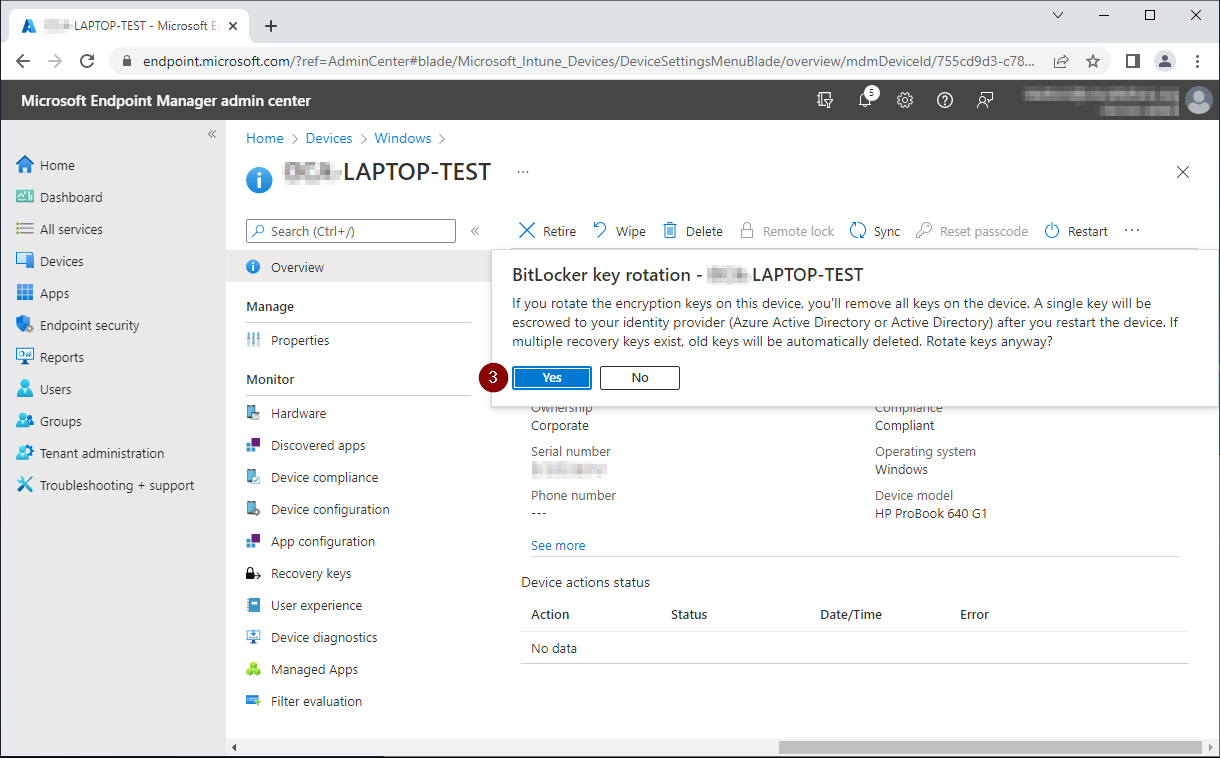
Rotate BitLocker recovery keys using Endpoint Manager
Devices - Windows
Select device - open menu - BitLocker key rotation
BitLocker policy settings for automatic key rotation
Enabling this option in the Endpoint Manager disk encryption policy will automatically rotate BitLocker recovery keys after they have been used on a client device.
Configure client-driven recovery password rotation: Enable rotation on Azure AD and Hybrid-joined devices.
References:
BitLocker overview
https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-overviewManage BitLocker policy for Windows devices with Intune
https://docs.microsoft.com/en-us/mem/intune/protect/encrypt-devicesUsing BitLocker recovery keys with Microsoft Endpoint Manager - Microsoft Intune
https://techcommunity.microsoft.com/t5/intune-customer-success/using-bitlocker-recovery-keys-with-microsoft-endpoint-manager/ba-p/2255517Enabling BitLocker with Microsoft Endpoint Manager - Microsoft Intune
by Author
https://techcommunity.microsoft.com/t5/intune-customer-success/enabling-bitlocker-with-microsoft-endpoint-manager-microsoft/ba-p/2149784


















Comments