Setup SSH Key Based Authentication on Debian from Windows
How to setup SSH Key Based Authentication on Debian 11 "Bullseye". Create and manage SSH keys using ssh-keygen from Windows 10 PowerShell. Copy public keys to the server and connect using SSH keys.
TL;DR
Too long, didn't read version.
Public and Private Keys
- Create a separate key pair for each device/workstation that will connect to the server.
- Always use passphrases to secure your SSH keys and save the passphrase in your password manager.
- Only the public key should be copied to the server. The private key should be saved on the client and never shared.
- If your device supports ED25519 then this is the best choice. If not, then use RSA with a key size of 4096 bits.
Manage SSH keys using ssh-keygen on Windows
# Create and manage SSH keys using ssh-keygen from Windows PowerShell # Create an ED25519 key pair with a comment ssh-keygen -t ed25519 -C "admin-user@work-laptop" # Create a 4096 bit RSA key pair with a comment ssh-keygen -b 4096 -C "admin-user@work-laptop" # Check the size of an existing key ssh-keygen -lf C:\Users\Username\.ssh\id_rsa # Change the passphrase of a private key file without creating a new key ssh-keygen -pf C:\Users\Username\.ssh\id_rsa
Copying public keys to the server
On the server, the public key will be added to the users home directory authorized_keys file.
/home/username/.ssh/authorized_keys
Copy public key using ssh-copy-id (Linux)
ssh-copy-id -i ~/.ssh/id_ed25519.pub admin-user@server-name
Copy public key manually (Windows)
# create .ssh directory and change the permissions, 700 means only the owner can read, write and execute mkdir ~/.ssh chmod 700 ~/.ssh # upload the public key file to the server /home/username directory # append contents of the public key to the authorized_keys file cat ~/id_ed25519.pub >> ~/.ssh/authorized_keys # remove the public key file rm ~/id_ed25519.pub # change permissions on authorized_keys, 600 means only the owner can read and write the file chmod 600 ~/.ssh/authorized_keys
Delete a public key
To delete a public key, remove it from the authorized_keys file
nano ~/.ssh/authorized_keys
SSH key based authentication
SSH key-based authentication uses a private/public key pair to log on to the server instead of a username and password. SSH keys are more secure than passwords because passwords can be brute force attacked, SSH keys cannot.
To gain access to the server, an attacker would need to get the private key file which, is only on your workstation. Getting the private key file is much more difficult than remotely brute force guessing your SSH password.
Public and Private Keys
- The public key is used to encrypt and, only the private key can decrypt.
- The private key is kept on the client.
- Private keys should be kept secret and should never be shared.
- The public key is stored on the server and can be shared freely.
- Create SSH keys on the device that will be using them, don't copy or transfer private keys between computers.
- Create a separate key pair for each device/workstation that will connect to the server.
- Always use passphrases to secure your SSH keys and save the passphrase in your password manager.
Give the key pair a name that identifies the admin user, client device and server that it is used to connect to e.g. admin-user@work-hp-laptop_web-server
This way, if a key gets compromised, you can easily identify which key needs to be de-authorized.
If you have multiple devices and key pairs and one is compromised or lost, you can connect to the server from another device and create a new key pair.
If you only have one private key, you should save it in your password manager.
It's important to properly manage and secure your SSH private keys!
Create SSH authentication keys
SSH keys can be created and managed on Linux and Windows PowerShell using the ssh-keygen command.
You can specify the authentication key type, number of bits and add a comment to the key when running ssh-keygen.
Reference:
ssh-keygen
by Author
OpenSSH authentication key utility
https://manpages.debian.org/bullseye/openssh-client/ssh-keygen.1.en.html
SSH authentication key types
Which SSH authentication key type should you use?
RSA- ssh-keygen defaults to using RSA
- Created in 1978, RSA is an old algorithm that is widely used
- Most compatible with SSH clients and servers
- Requires a larger key size to be more secure/stronger
- Generate an RSA key with a larger key size using the -b option
- In the future, RSA may not be secure as processing power increases
ssh-keygen -b 4096
ECDSA
- An algorithm created by the US government agency NIST in 1992
- Supports three key sizes 256, 384 and 521 bits
- Most SSH clients and servers will support ECDSA
- There may be political and privacy concerns about using a US government standard
ssh-keygen -t ecdsa -b 521
- A newer algorithm created in 2011 based on elliptic curve cryptography
- Mathematically strong and fast
- Some clients might not support ED25519
- There is no key size option as all ED25519 keys are 256 bits
ssh-keygen -t ed25519
If your device supports ED25519 then this is the best choice. If not, then use RSA with a key size of 4096 bits.
In this guide, we will use two examples: One creating a 4096 bit RSA key pair and one creating an ED25519 key pair.
Create an RSA key pair
- You should create the SSH authentication key from the client workstation that it will be used on.
- The simplest way to create an SSH key pair is to run the ssh-keygen command.
- Running ssh-keygen without specifying any options will generate a 3072 bit RSA key pair.
In this example, I'm using Windows 10 and PowerShell to create the SSH key pair.
You'll be asked where to save the key files - press enter to accept the default location C:\Users\Username\.ssh
Enter a passphrase for your SSH key - save the passphrase in your password manager.
# Create a 4096 bit RSA key pair ssh-keygen -b 4096
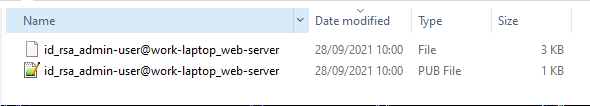
The private/public key pair has been created in your user folder. The .pub file is the public key that will be copied to the server. The key type id_rsa is also included in the filename
Because I'm using multiple SSH key pairs, I will rename the key files adding my admin username, client device and server hostname at the end. This way, I can easily identify the admin user, workstation and server that the key pair is used for connecting to.
e.g. id_ecdsa_admin-user@work-laptop_web-server
Create an ED25519 key pair
The following PowerShell command will create a 256 bit key pair using the ED25519 algorithm with a comment
There is no need to specify the key size as all Ed25519 keys are 256 bits
-t Specifies the type of key to create e.g. Ed25519
-C Comment or name for the key
# Create an ED25519 key pair ssh-keygen -t ed25519 -C "admin-user@work-laptop"
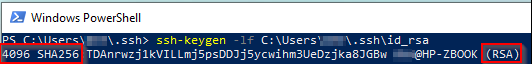
Check the size of an existing key
Show private key file fingerprint
-l show fingerprint
-f filename
ssh-keygen -lf C:\Users\Username\.ssh\id_rsa
Change the private key passphrase
-p change the passphrase of a private key file without creating a new key
-f filename
ssh-keygen -pf C:\Users\Username\.ssh\id_rsa
Copy public key to the server
Copy public key using ssh-copy-id (Linux)
On Linux, you can use the command ssh-copy-id to copy the public key to a server. You will be prompted for an admin user password.
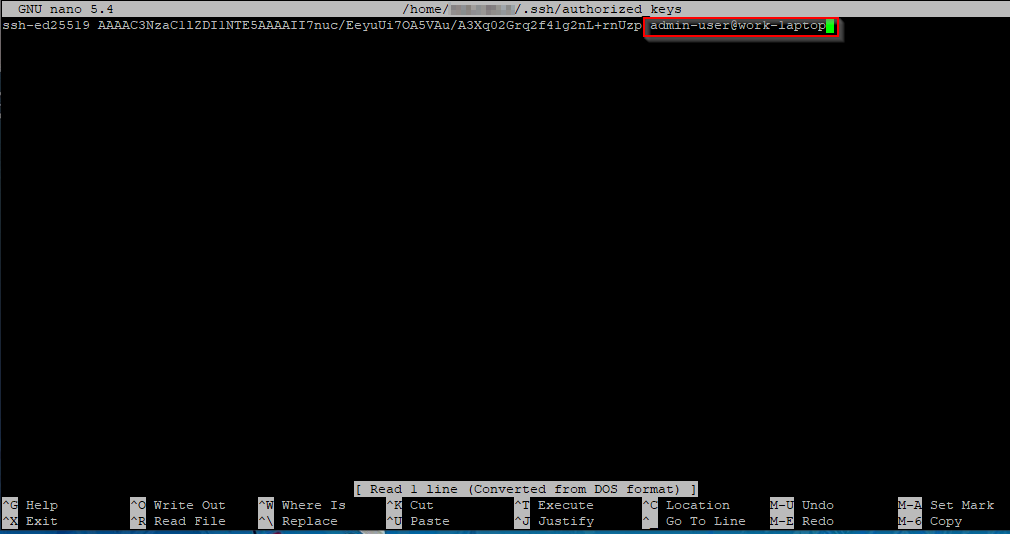
On the server, the public key will be added to the users home directory authorized_keys file.
/home/username/.ssh/authorized_keys
-i identity_file
ssh-copy-id -i ~/.ssh/id_ed25519.pub admin-user@server-name
Copy public key manually (Windows)
There is no ssh-copy-id command on Windows so you will need to complete these steps manually.
Use SSH to connect to the server, create the .ssh directory then upload the public key file and add it to the authorized_keys file.
# create .ssh directory and change the permissions, 700 means only the owner can read, write and execute mkdir ~/.ssh chmod 700 ~/.ssh # upload the public key file to the server /home/username directory # append contents of the public key to the authorized_keys file cat ~/id_ed25519.pub >> ~/.ssh/authorized_keys # remove the public key file rm ~/id_ed25519.pub # change permissions on authorized_keys, 600 means only the owner can read and write the file chmod 600 ~/.ssh/authorized_keys
Delete a public key
To delete a public key, remove it from the authorized_keys file
nano ~/.ssh/authorized_keys
You can see the public key fingerprint and comment identifying the user and client device.
Connect to the server using SSH keys





Comments